There are many reasons why you would want to implement route filtering. A good example would be to prevent routes to transit networks being advertised to a branch router, because no host in the branch would ever need to send packets to a host in the transit network.
Filtering in EIGRP is configured using the distribute-list router subcommand, which can reference either a prefix list, an ACL or a route map to determine whether or not routes should be filtered, and in which direction and (optionally) on which interface.
Here’s our network for this lab:
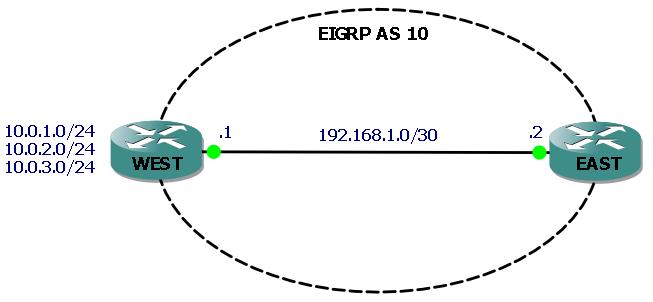
The three networks attached to router WEST (represented by loopback interfaces) are the ones we will filter routes to, so that they do not appear in router EAST’s routing table. We’ll filter each route in turn using the distribute-list command plus a prefix list, an ACL and a route map.
Without any filtering, each route appears in the routing table of router EAST:
EAST#sh ip route eigrp
10.0.0.0/24 is subnetted, 3 subnets
D 10.0.2.0 [90/156160] via 192.168.1.1, 00:31:12, FastEthernet0/0
D 10.0.3.0 [90/156160] via 192.168.1.1, 00:31:04, FastEthernet0/0
D 10.0.1.0 [90/156160] via 192.168.1.1, 00:31:21, FastEthernet0/0
Example 1 – filter route to 10.0.1.0/24 using a prefix list:
IP prefix lists examine both the route prefix (subnet number) and the prefix length (subnet mask) for a match. IP prefix lists consist of a command with a sequence number and a permit/deny action. Route prefixes are matched by the command’s prefix/prefix length parameters and prefix lengths are matched by the optional ge (greater than or equal) and le (less than or equal) parameters. If neither ge or le is specified then the prefix length is matched exactly.
In our example we will use a prefix list to exactly match the route to 10.0.1.0/24 and deny it, and then to permit all other routes. First we create the IP prefix list:
ip prefix-list West-PF seq 10 deny 10.0.1.0/24 ip prefix-list West-PF seq 20 permit 0.0.0.0/0 le 32
Command sequence number 10 exactly matches the prefix/prefix length with a deny statement. Sequence 20 uses 0.0.0.0/0 to match all other prefixes and le 32 to match prefix lengths 0-32, which effectively means “match all other routes” and permit them.
We then configure EIGRP with a distribute-list command that references the prefix list and is applied outbound:
WEST#sh run | begin router router eigrp 10 network 10.0.0.0 network 192.168.1.0 0.0.0.3 distribute-list prefix West-PF out no auto-summary
To verify, the show ip protocols command is useful here:
WEST#show ip protocols Routing Protocol is "eigrp 10" Outgoing update filter list for all interfaces is (prefix-list) West-PF
If we now check EAST’s routing table we will see that the route to the 10.0.1.0/24 network has been filtered by router WEST and no longer appears in the routing table:
EAST#sh ip route eigrp
10.0.0.0/24 is subnetted, 2 subnets
D 10.0.2.0 [90/156160] via 192.168.1.1, 00:12:37, FastEthernet0/0
D 10.0.3.0 [90/156160] via 192.168.1.1, 00:12:37, FastEthernet0/0
Example 2 – filter route to 10.0.2.0/24 using an ACL:
ACL’s use statements referencing an IP address and a wild card mask, followed by a permit/deny action. Remember that as with prefix lists you must also have a statement permitting the other networks that you don’t want to filter. So lets configure our ACL to deny 10.0.2.0/24:
access-list 1 deny 10.0.2.0 0.0.0.255 access-list 1 permit any
It’s worth noting at this point that you cannot have multiple distribute-list commands in your router configuration, and if we try to add our new one without removing the previous command, we get the following:
WEST#conf t Enter configuration commands, one per line. End with CNTL/Z. WEST(config)#router eigrp 10 WEST(config-router)#distribute-list 1 out % Prefix-list filter exists, de-config first
So, after removing our previous distribute-list command we can add our new one that references our ACL:
WEST(config-router)#distribute-list 1 out
EAST’s routing table now confirms that WEST is not advertising the route to 10.0.2.0/24:
EAST#sh ip route eigrp
10.0.0.0/24 is subnetted, 2 subnets
D 10.0.3.0 [90/156160] via 192.168.1.1, 19:23:34, FastEthernet0/0
D 10.0.1.0 [90/156160] via 192.168.1.1, 00:01:20, FastEthernet0/0
Example 3 – filter route to 10.0.3.0/24 using a Route Map:
Route Maps have many uses and consist of a set of commands that are processed sequentially. For the purposes of filtering routes in EIGRP we can use a route map that references either an ACL or a prefix list when looking for matches on routes to filter. In this example we’ll create a route map that matches the 10.0.3.0/24 route based on a simple ACL.
First we create the ACL with a single permit statement to match our route:
access-list 2 permit 10.0.3.0 0.0.0.255
Then we create our route map (named Filter-10.0.3.0/24, so we know what it does) with a deny statement that will match IP addresses based on access list 2. Note we also have a permit statement that when used without any match statements, means “match all” effectively permitting all other routes:
route-map Filter-10.0.3.0/24 deny 10 match ip address 2 ! route-map Filter-10.0.3.0/24 permit 20
Finally, we configure EIGRP to use a distribute-list with the route map:
WEST(config-router)#distribute-list route-map Filter-10.0.3.0/24 out
EAST’s routing table now confirms that WEST is not advertising the route to 10.0.3.0/24:
EAST#sh ip route eigrp
10.0.0.0/24 is subnetted, 2 subnets
D 10.0.2.0 [90/156160] via 192.168.1.1, 19:23:34, FastEthernet0/0
D 10.0.1.0 [90/156160] via 192.168.1.1, 00:01:20, FastEthernet0/0
I hope this has been a useful explanation. Thanks for reading, and good luck with your CCNP studies!
Rich
Follow Rich on Twitter
Nicely explained
Thanks Shabeer!
the simplest example of route filtering in Eigrp , this is the one of the easiest explanation that i found in web
the OCG book is crap in front of this
thanks rich
Thanks Gaurav! That’s a really nice comment. Glad you found it useful.
Rich
Easiest and simplest example of route map … great man !!! tnx
Thanks Miran! Glad you found it useful
simply the best! this is exactly what I looking for.
Thanks boridza!
Simple explanation that non-networking guy can also understand. Thanks Rich.
Thanks for the comment Punith!
Rich
Thank you very much for this. It’s a very simple explanation for potentially complicated configs. I really appreciate you putting this stuff up here for everyone to learn from!
Thank you very much for this excellent explanation
excellent and easily understandable work ….thankyouuuu
Hello Rich
The explanation about prefix list and ACL was just impeccable.
But I got lost with Route Map.
Firt we had created a simple access list which has a permit statement.
access-list 2 permit 10.0.3.0 0.0.0.255
Now when we create a route map with a “Deny” statement, what does this deny do?
route-map Filter-10.0.3.0/24 deny 10
And then we have a match statement to permit the access list.
Can you please explain?
Thanks.
Oh my God! God Bless You Rich! This is the simplest example I have ever found On the Internet, Thank You So Much for this! It was really a great help
How the central sites( Site A & Site B ) will know the route , if there are two MPLS links on site router connected over GRE Tunnels and how the IP address assignment will be done on site location , do we need to put static IP on PCs