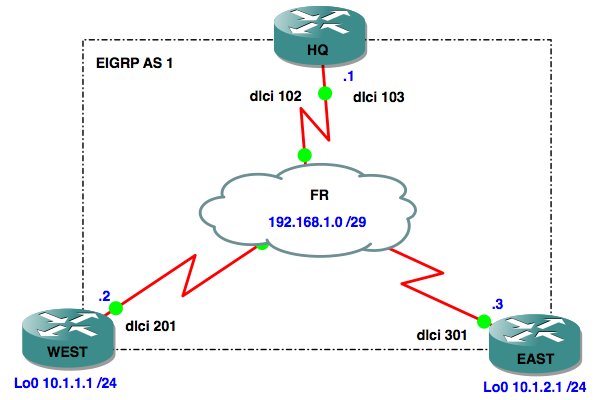
In certain situations an engineer may need to manipulate EIGRP metrics, and one method is to use Offset Lists to increase both the AD (Advertised Distance) and FD (Feasible Distance) of a route by a certain value – the offset.
Offset List configurations define the following:
- route(s) that we want to amend the metric for (matching an ACL)
- direction of the updates being sent or received
- interface on which updates are sent or received
- offset integer value
Network diagram:
Objective One:
when router WEST advertises prefix 10.1.1.0 out of interface Serial0/0, it should add 100 to the metric
Lets first check the FD and AD values that HQ has in its topology table for prefix 10.1.1.0/24:
HQ#sh ip eigrp topology 10.1.1.0/24
IP-EIGRP (AS 1): Topology entry for 10.1.1.0/24
State is Passive, Query origin flag is 1, 1 Successor(s), FD is 2297856
Routing Descriptor Blocks:
192.168.1.2 (Serial0/0), from 192.168.1.2, Send flag is 0x0
Composite metric is (2297856/128256), Route is Internal
Next, we’ll configure the offset list on router WEST:
WEST(config)#access-list 10 permit 10.1.1.0 WEST(config)#router eigrp 1 WEST(config-router)#offset-list 10 out 100 serial 0/0
If we check the FD and AD values on the HQ router again, we’ll see they have both increased by 100:
HQ#sh ip eigrp topology 10.1.1.0/24
IP-EIGRP (AS 1): Topology entry for 10.1.1.0/24
State is Passive, Query origin flag is 1, 1 Successor(s), FD is 2297856
Routing Descriptor Blocks:
192.168.1.2 (Serial0/0), from 192.168.1.2, Send flag is 0x0
Composite metric is (2297956/128356), Route is Internal
Objective Two:
when HQ router receives an advertisement for prefix 10.1.2.0 in via interface Serial0/0, it should add 100 to the metric
Lets first check the FD and AD values that HQ has in its topology table for prefix 10.1.2.0/24:
HQ#sh ip eigrp topology 10.1.2.0/24
IP-EIGRP (AS 1): Topology entry for 10.1.2.0/24
State is Passive, Query origin flag is 1, 1 Successor(s), FD is 2297856
Routing Descriptor Blocks:
192.168.1.3 (Serial0/0), from 192.168.1.3, Send flag is 0x0
Composite metric is (2297856/128256), Route is Internal
Next, we’ll configure the offset list on router HQ:
HQ(config)#access-list 10 permit 10.1.2.0 HQ(config)#router eigrp 1 HQ(config-router)#offset-list 10 in 100 serial 0/0
If we check the FD and AD values on the HQ router again, we’ll see they have both increased by 100:
HQ#sh ip eigrp topology 10.1.2.0/24
IP-EIGRP (AS 1): Topology entry for 10.1.2.0/24
State is Passive, Query origin flag is 1, 1 Successor(s), FD is 2297856
Routing Descriptor Blocks:
192.168.1.3 (Serial0/0), from 192.168.1.3, Send flag is 0x0
Composite metric is (2297956/128356), Route is Internal
I hope this has been a useful explanation. Thanks for reading, and good luck with your CCNP studies!
Rich
Follow Rich on Twitter